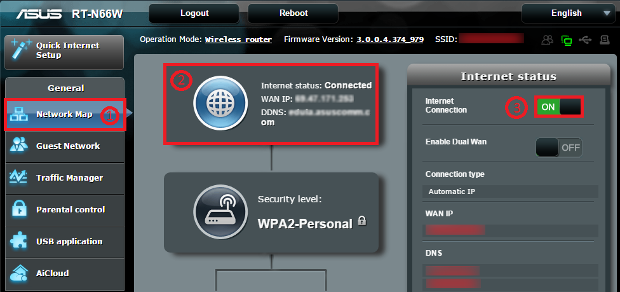
Proxy server is a computer that sits between a client computer and
the Internet, and provide indirect network services to a client. It may
reside on the user's local computer, or at various points between the
user's computer and destination servers on the Internet. A proxy server
intercepts all client requests, and provide responses from its cache or
forwards the request to the real server. A client computer is connected
to the proxy server, which acknowledges client requests by providing the
requested resource/data from either a specified server or the local
cache memory. Client requests include files or any other resources
available on various servers.
Types of Proxy servers
Proxy servers are classified into several types based on purpose and
functionality. Some of the most common types and their uses can be
described as below:
Web Proxy is the most common type of proxy
application, which responds to the user requests by accessing resources
from cached web pages and files available on remote web servers. This
facilitates quick and reliable access to data for local network clients.
If the requested resource is not found in the cache, then a web proxy
fetches the file from the remote server, and saves a copy in the cache
before returning it to the client.
Transparent Proxy is mostly used for caching
websites and overcoming simple IP bans. However, such proxies do not
provide any user anonymity since user’s original IP address is exposed.
Transparent proxies are not specifically configured on the client
computers.
Anonymous proxies do not hide the original IP
address of the user; however, they provide adequate anonymity to most
users. Anonymous proxies are easily detectable.
A
distorting proxy, identifies itself as a proxy server, and modify the HTTP headers to disguise the original IP address.
Tunneling proxies are capable of passing client
requests and return responses without making any modifications. These
are also referred to as gateway proxies.
A
forward proxy responds to client requests by
retrieving data from a wide range of sources on the internet. It is also
referred to as an Internet-facing proxy.
Open proxies belong to the category of forwarding
proxy servers, which are accessible by any internet user since they can
receive and return requests from any client computer. Meanwhile,
anonymous open proxies are used for user anonymity to conceal the IP
address.
Reverse proxies, also known as surrogates, usually
receive requests from the Internet and forward them to internal network
servers. A reverse proxy server forwards requests to one or more proxy
servers, whose response is returned to the client computer, the user of
which has no knowledge on the origin of the response.
Where is a Proxy server used?
Proxy servers are used for several purposes. If it is used as a
caching web proxy, it can dramatically improve performance of a web
response. When a request is made by a client, a caching proxy returns
response directly from its cache if the document already exists.
Otherwise, it makes the request to the real server, returns the result,
and save it in its cache for later use.
Proxy servers are also used as "web proxies" to filter web page
contents. An organization or company may use a proxy server to block
offensive web contents from viewed by the users. Considering the growing
need within organizations to prevent employees from accessing specific
websites, such as facebook.com, proxy servers are being deployed across
the computers connected to the intranet. Some web proxies are able to
reformat web pages to suit a specific set of audience, or cater certain
organizational or personal internet usage purposes. Further, web proxies
can be used to prevent the attack of computer viruses and malware, as
well as other hostile content transferred across the internet web pages.
However, users can also use web proxy servers to access those blocked
sites indirectly. These web proxies are built with PHP or CGI to
implement the proxying functionality, and provide web access to those
sites blocked by corporation and school proxies. Moreover, Internet
Service providers (ISPs) may also use proxies to block computer viruses
and other offensive contents.
There are several advantages of Proxy servers. We intend to provide some of the most basic uses of proxy servers.
Performance Improvement:
Proxy servers also contribute to improved web performance since the
results of the user requests are saved in cache memory for a set period
of time. This is achieved with the help of a caching proxy server, which
could save a large amount of time while catering to the requests from a
vast user load. A caching proxy server maintains a local copy of
frequently requested web content. Hence, it can accelerate service
requests by retrieving content from the cache memory, if it had already
been requested by another client on the same network. This feature
contributes to a significant reduction in upstream bandwidth usage and
costs for large organizations with thousands of employees.
Monitoring and Filtering User Requests:
As discussed earlier, web proxies can be used to filter user
requests, and block certain content or web pages from being accessed.
This can be achieved with the help of a content-filtering web proxy
server that differentiates the users’ level of control over the content,
based on the user type - Guest or Administrator.
Content-filtering proxies are generally used in organizations and
educational institutions with strict internet-usage policies. Blocking
certain websites, and restricting access to specific key words and
censoring undesirable content are some of the basic features provided by
content-filtering or web-filtering proxies. However, there are certain
web proxies that are used to bypass geo-restrictions and censorship
regulations by using certain advanced services that help access
resources from blacklisted web locations.
Anonymous Browsing:
An anonymous proxy server is another type of web proxy that
anonymizes users' online activities. This type of proxy server directs
the user requests to a destination server, which ultimately has no
knowledge of the source of the request. Only the proxy is aware of the
source of the request, including the user IP address and location.
Advertisements targeting specific geographical regions
Web Proxies can also be used to validate and verify geo-targeted
advertisements. Servers of such ads validate the source IP address of
the user request, and determine the geographic location of the request
with the help of a geo-IP database. The user requests are responded via
proxy servers that are located within the respective geographical
location, to ensure that advertisements displayed are purely relevant to
the users’ location.
Translation:
Considering the global audiences, translation proxies have been
developed to localize/translate the content of a source website into a
local language of the client computer. Responses for requests sent by
local users are replaced with translated content from the source
website, and passed back through the proxy server. Some translation
proxies also provide additional services such as excluding source
content or substituting source content with original local content.
Conclusion
The most popular proxy server used today is a Web Proxy, and it is
used to filter contents and allow anonymous browsing. Being able to
unblock geo-restricted content is also a wide used application for using
public web proxies.
Although proxies provide anonymous browsing and content filtering, they
are mostly limited to web browsing and also lack security. For secure
and encrypted communication with privacy protection, we recommend
VPN solution.
If you have any questions about Proxy Server, please post your question on
Proxy Server Forum.
Reference: Wikipedia